LAPS is automatically installed on Windows Server 2022 and later versions of Windows Server 2019. It can be a good idea for AD environments to enable it so in the event a local admin password is compromised, it can automatically be changed or in situations where administrators do not have to remember the passwords of each local admin on each domain joined devices. There are 2 options: 1 for Active Directory or Azure Active Directory environments. Below is step by step directions for Active Directory environments.
Prerequisites
- Add LAPS.adml and LAPS.admx files to Policy Definitions via SYSVOL.
- Update Domain Functional Level to Domain Functional Level of 2016 if necessary. LAPS will not run properly if not. If you are on a Domain Functional Level of 2016 and have Windows Server 2019 or 2022 Domain Controllers, you can use all the features of Windows LAPS.
- The versions of Windows and Windows Server required to use Windows LAPS:
- Windows 11 Professional, Education, or Enterprise
- Windows 10 Professional, Education, or Enterprise
- Windows Server 2022 and Windows Server Core 2022 Windows Server 2019
Check for the PowerShell Module
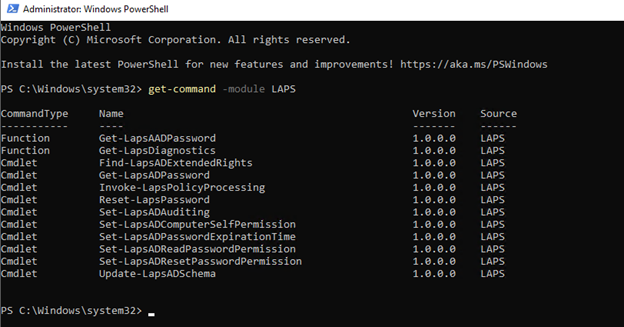
The PowerShell module should already be included if using Windows Server 2019 and above. If you would like to double check run the command: get-command -module LAPS from PowerShell on the windows AD server. Install the module if you do not have it.
Extend the Active Directory Schema
You must extend the Schema with new attributes. You must be a schema admin to run the command: Update-LapsADSchema -verbose
The verbose command will show details of what the command is doing. After running the command, type “A” to add all the schema extensions that are needed.
Verify the Schema was Extended
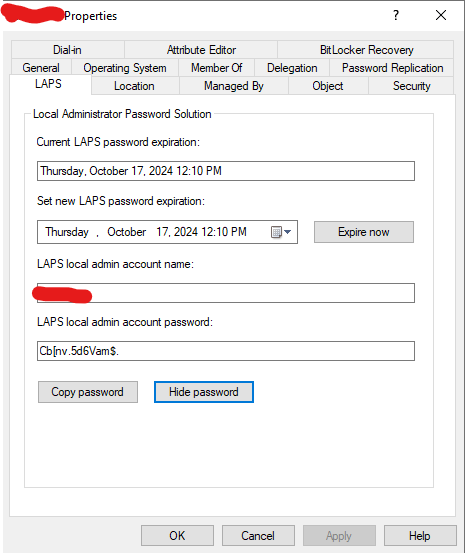
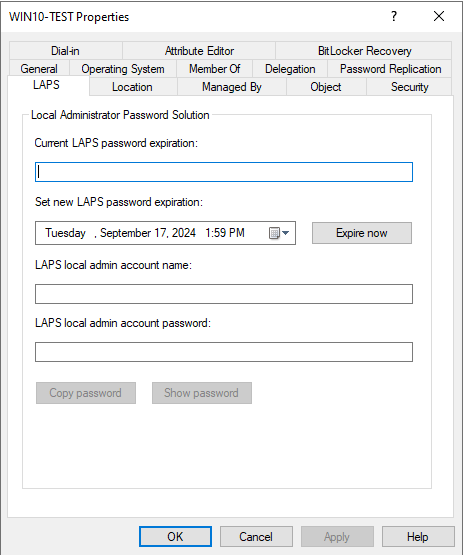
If the Schema was Extended, there will be a new LAPS tab will you view the Properties of a computer in Active directory Users and Computers.
Set the AD LAPS Computer Permission
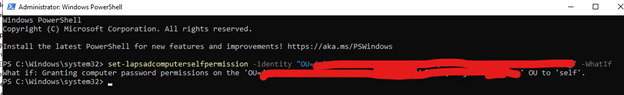
Provide permission to the OU or OUs where the computers are housed to change computer passwords. The command is:
set-lapsadcomputerselfpermission –identity “<Name of OU>” May need the full distinguished name
Configuring Group Policy
- Open group policy editor
- Create new Computer Policy
- Edit the policy and navigate to “Computer Configuration -> Policies -> Administrative Templates -> System -> LAPS”
Group Policy Configs
Configure Password Backup Directory (required)
With this group policy setting you determine if the password is going to be stored in Active Directory, or Azure Active Directory (Entra ID).
Password Settings (required)
This policy setting determines the password complexity, password length, and password age in days.
Enable Password Encryption (required)
This setting determines if passwords will be encrypted when they are stored in Active Directory.
Configure Authorized Password Descriptors (optional)
This setting determines the specific user or group who is authorized to decrypt encrypted passwords.
Name of Administrator Account to Manage (optional)
This setting specifies a custom Administrator account for which to manage the password if you are using an account that is not the built in Administrator account.
Do not Allow Password Expiration Time Longer than Required by Policy (optional)
With this setting, passwords are not allowed to have expiration times that are beyond the age dictated by the “password settings” policy.
Post-authentication Actions (optional)
This setting determines the actions to take after the administrator password has been used, and the grace period before the action is taken in hours.
Verifying Success and Retrieving Passwords
After you have configured the group policy, run gpupdate /force on the computer that this is applied to and allow group policy to update. If everything is working correctly you will see password information in your Active Directory Users and Computer Object.